PacketCYBER EVA provides visibility and insight into how encryption
is used across the enterprise and provides advanced threat visibility.
PacketCYBER EVA provides actionable insights and intelligence on encrypted traffic, without requiring decryption, to help enterprises define, measure, monitor, and maintain encryption standards and identify issues.
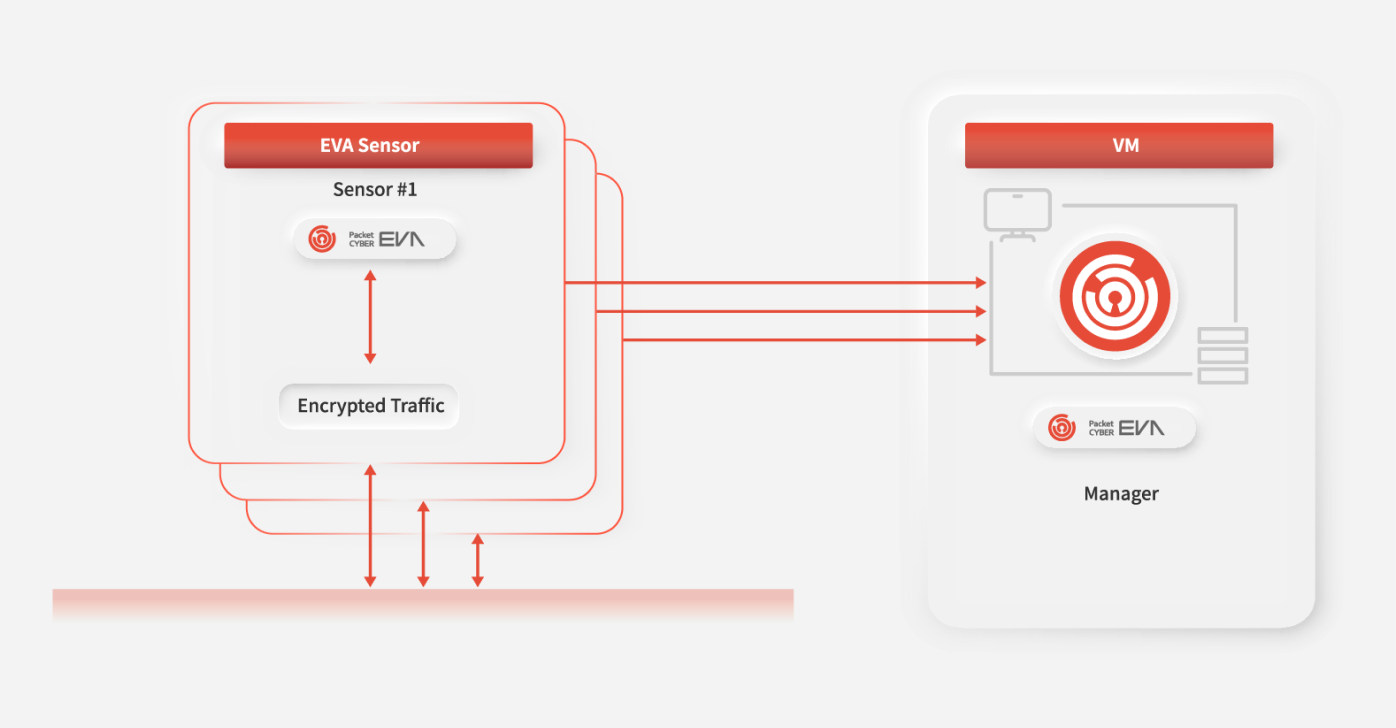
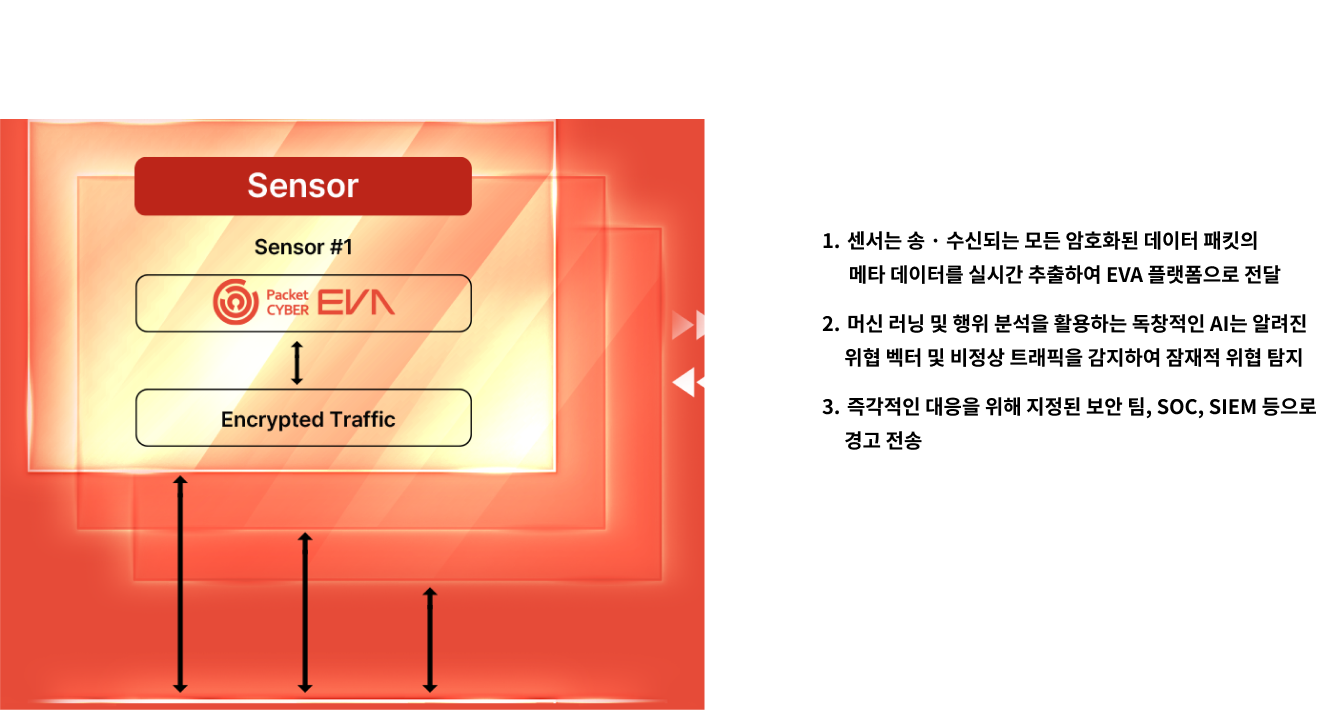
[PacketCYBER EVA] Sensor, Manager
 Key Benefits (Only PacketCYBER EVA)
Key Benefits (Only PacketCYBER EVA)