Real-time TLS Visualization
and Threat Detection
- Obsolete encryption protocols with weak security
e.g. TLS1.0, TLS1.1, SSL1.0, SSL2.0, etc.
- Weak cryptographic algorithms
e.g. NULL, RC2, RC4, DES, IDEA and TDES/3DE
- Deprecated key exchange mechanisms
e.g. using keys less than 1024bits RSA and DHE, ANON, EXPORT
- Expired or imminent expiration certificates
Real-time File inflow and outflow
and Malware Detection
- Machine Learning (ML)
- File reputation
- YARA Rule
- Mal-doc detection scripts
Real-time Attacker TTP Detection
- Port scanning
- Address scanning
- Web-based malware transmission
- Email-based malware transmission
- Dre-by-download behavior
- SSH password brute force attack
- FTP password brute force attack
- RDP password brute force attack
- Network intrusion (exploit)
- Application Exploit
- Suspicious outward-facing communications
- Covert Channe
- C&C detection
- C&C evasion technology (DGA/Fast-Flux)
- Suspicious data leak(Large Upload)
- SSL/TLS fingerprint-based malware detection


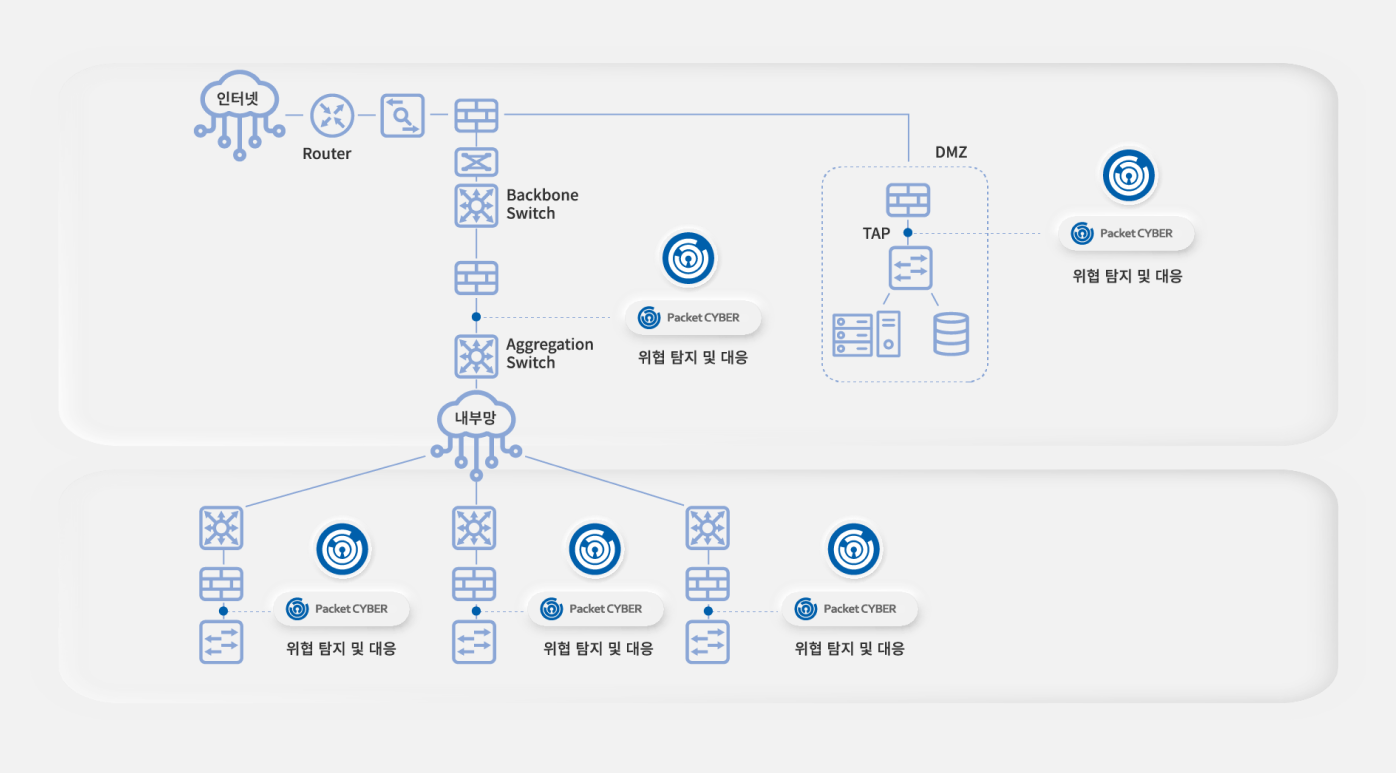
 Key Features (Only PacketCYBER)
Key Features (Only PacketCYBER)